- 27 Mar 2023
- 2 Minutes to read
- Print
How to Configure Suspicious Objects Monitor & Prevention Modes for Edge Series Devices
- Updated on 27 Mar 2023
- 2 Minutes to read
- Print
Summary
Suspicious Objects (SO) are suspicious IP addresses (Nodes) or network connections (Links) to be blocked on the Edge series devices, including EdgeIPS, EdgeIPS Pro, and EdgeFire. The suspicious objects are imported to EdgeOne from the external SO sources, such as third-party products, via the Suspicious Object API keys. There are two security modes for SO, “Monitor Mode” and “Prevention Mode”, aiming to decide whether or not the device will take action when a threat or an attack is detected.
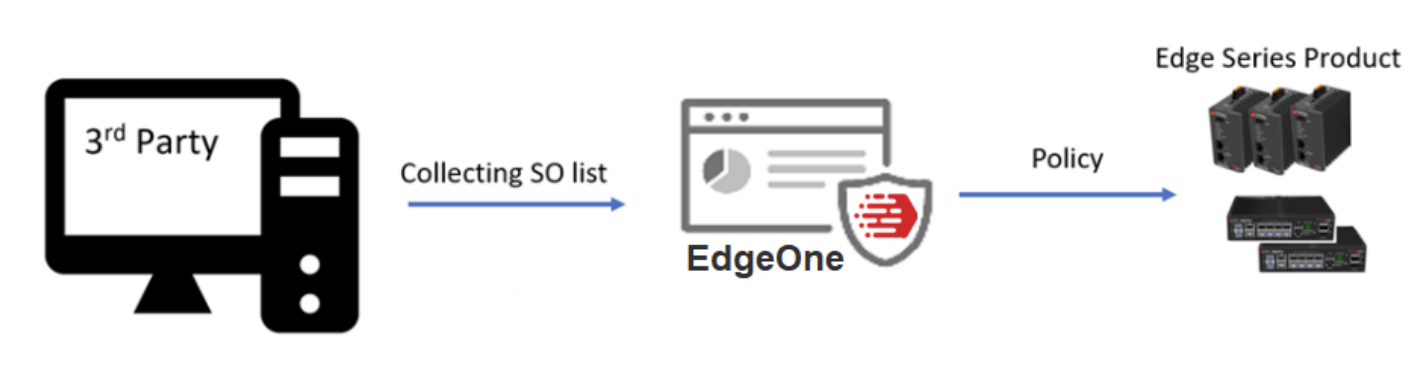
If the suspicious object operation mode is “Monitor Mode”, the device will not take any action but generate logs when the suspicious object rules are matched. The monitor mode is recommended in the POC (Proof of Concept) or lab testing stage for security administrators to monitor threat detection results.
If the suspicious object operation mode is “Prevention Mode”, the device will take action to block the traffic and generate logs when the suspicious object rules are matched. The device could be switched to prevention mode in the production stage after the third-party suspicious object pool is verified by IT or OT team.
The following table summarizes the settings:
| Security Operation Settings | Suspicious Object Operation Mode | Action | ||
| Generate Logs | Allow the Traffic | Block the Traffic | ||
| Inline | Monitor | V | V | — |
| Prevention | V | — | V | |
| Offline (Mirror Traffic) | Monitor | V | V | — |
| Prevention | — | — | — | |
Applicable Version
All versions of EdgeIPS, EdgeIPS Pro and EdgeFire
Details
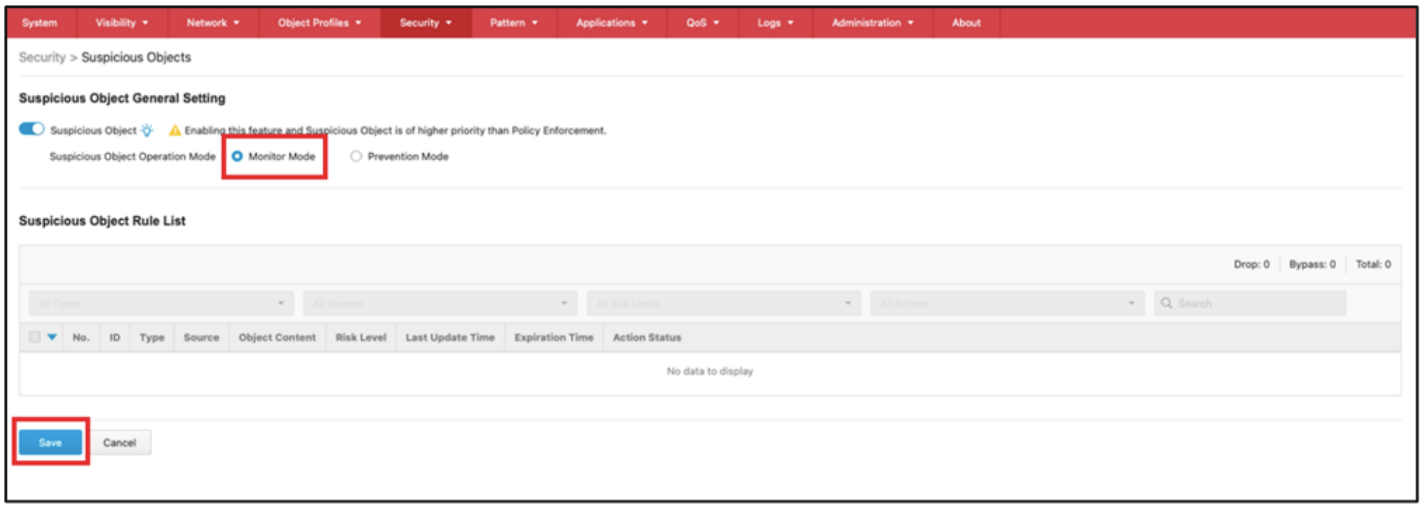
1. Configuring Monitor Mode for the Edge Device
- Access the web-based management console of the Edge device.
- Go to [Security] > [Suspicious Objects].
- Use the toggle to enable [Suspicious Objects].
- Select [Monitor Mode] for [Suspicious Object Operation Mode].
- Click the [Save] button to save the settings.
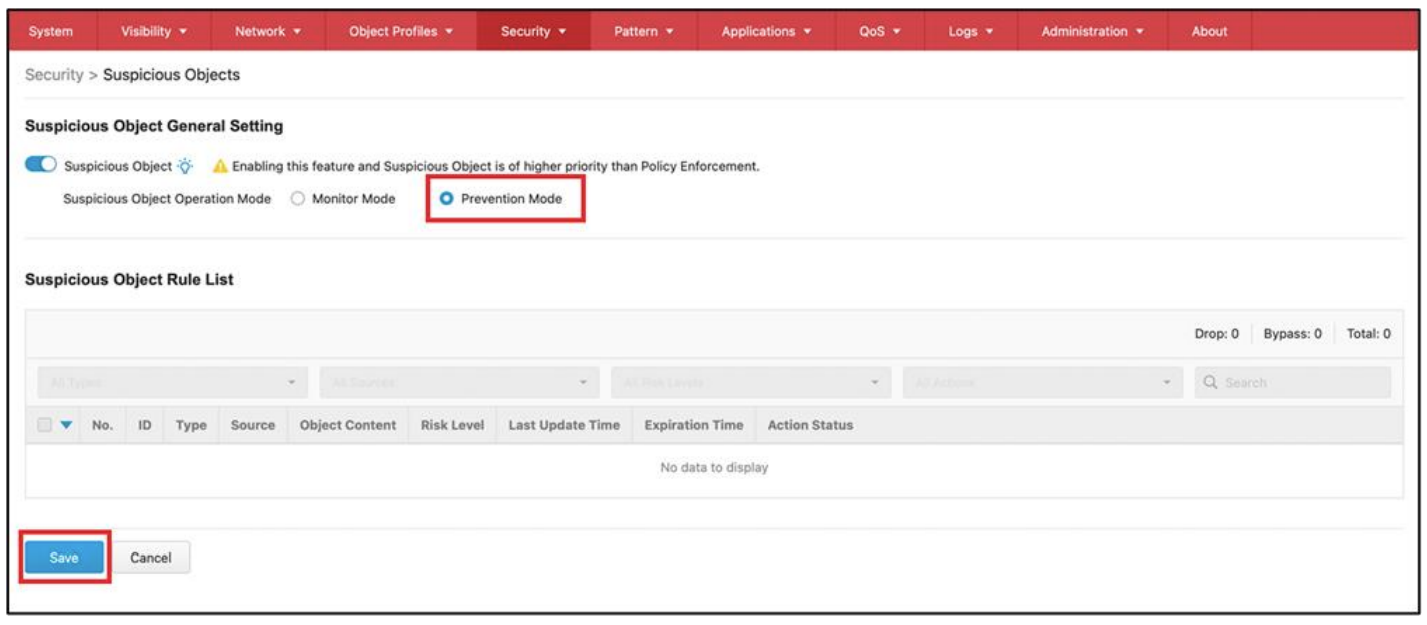
2. Configuring Prevention Mode for the Edge Device
- Access the web-based management console of the Edge device.
- Go to [Security] > [Suspicious Objects].
- Use the toggle to enable [Suspicious Objects].
- Select [Prevention Mode] for [Suspicious Object Operation Mode].
- Click the [Save] button to save the settings.
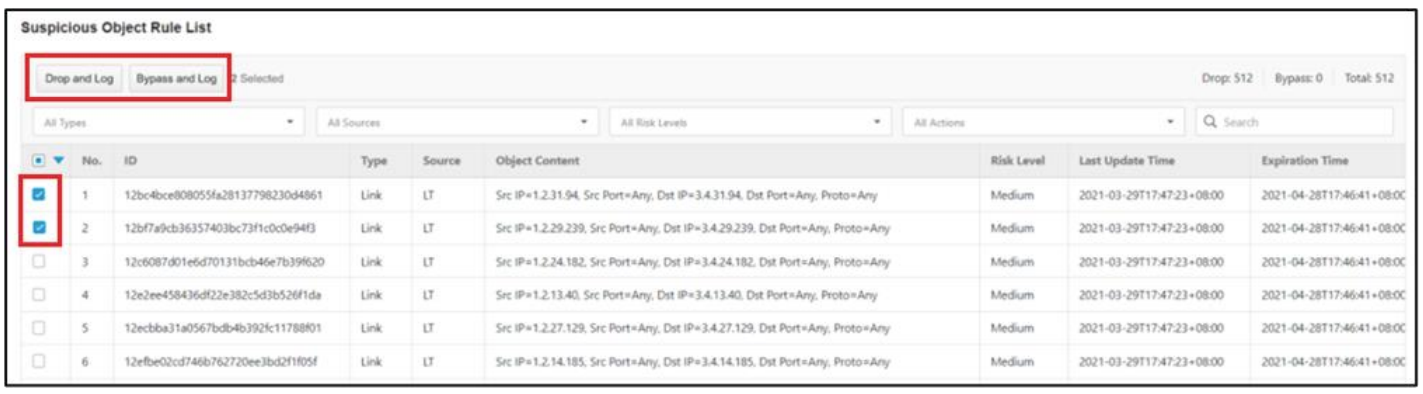
3. Changing the Action of Suspicious Object for the Edge Device
- Access the web-based management console of the Edge device.
- Go to [Security] > [Suspicious Objects] > [Suspicious Object Rule List].
- Select one or multiple suspicious objects and choose an action, [Drop and Log] or [Bypass and Log] for the time when the selected suspicious object rules are matched.
For support assistance, please Contact Us at support@txone.com or your Support Provider.