Product FAQ for TXOne Security Inspection Solution: ElementOne and Portable Inspector
This document collects and answers the most common questions about TXOne Security Inspection products, ElementOne and Portable Inspector that arise. Possible categories include, but are not limited to, Configuration, Deployment, Installation/Uninstall, Upgrade, Migration, Specification, License, etc.
Comparison
What is the difference between PI Pro and Standard Edition?
| PI Standard
|
PI Pro
|
|
| Supports Windows Scan | V | V |
| Supports Linux Scan | V | V |
| Management Program (ElementOne) | V | V |
| Asset Info Collection | V | V |
| Secure Storage | N/A | V 64G |
| AES-256 Hardware Encryption | N/A | V |
| Storage size for logs and quarantined files | 16G | 64G |
Specifications
1. How does PI ensure data integrity?
- HARDWARE: The PI USB is a customized proprietary hardware which provides all-time read-only protection. No user or program can read or alter this protection.
- SOFTWARE: PI utilizes Microsoft Windows APIs to monitor all files operation on the PI data partition while PI is running. Any unauthorized files in the data partition will be deleted.
2. How does PI ensure confidentiality?
All confidential data is encrypted. In the scanning tool (USB stick), the encrypted data is kept in a hidden area that is invisible from the host system (both Windows and Linux).
3. What are the self-protection mechanisms or techniques used by PI to manage its hidden storage and quarantined files in order to protect itself from being infected or being used as a carrier to spread malicious files to other equipment?
PI’s partitions utilizes customized hardware to provide all-time read-only protection. No users nor programs are allowed to alter this protection mechanism. Meanwhile, PI also utilizes Microsoft Windows APIs to monitor all files operations on its data partition as it is running. Any unauthorized files in the data partition will be deleted automatically. Quarantined files are stored in a hidden partition where it can only be accessed by PI and cannot be read or overwritten by any OS or applications.
4. Please explain whether and how PI communicates with TXOne cloud.
PI scanning tool and/or management program only communicates with TXOne cloud for product registration/authentication and components update. No other data is sent to the cloud.
· Please contact us for more information on data collection.
5. What are the standards, certifications, or compliance measures fulfilled by PI?
For the PI USB hardware, we have achieved CE, FCC, VCCI, C-tick, BSMI, and RoHS & REACH compliance.Please contact us if you need more detailed information.
6. If the log partition of PI is full, does ST scanning still work?
When the LOG partition is full, the scan can still be performed by ST and won't be blocked. There will also be a warning message when ST starts to quarantine a file. For example: 'Unable to back up quarantined files because there is no more space on the USB device. Manually delete the infected files or export and delete logs from the USB device before trying again.' No log rotation for LOG partition as the current design.
7. What is the communication protocol between the Scanning Tool and ElementOne?
The default communication port for Scanning Tool to connect to the ElementOne is port 3030, and this can be changed through ElementOne settings.
8. Does ElementOne need internet connection?
Yes, ElementOne needs internet connection to obtain authentication, updates, and other supporting information. The information below shows the URLs that ElementOne server will reach out to and their purposes:
• Required ports
| Protocol | Port number | Purpose |
|---|---|---|
| TCP | 22 | SSH to ElementOne Vshell |
| TCP | 443 | ElementOne web console |
| TCP | 3030 | Device registration, communication, and AU (Default port) |
| TCP and UDP | 53 | DNS |
| UDP | 123 | NTP |
• Allowlist
Version : 1.18.0 and earlier
| FQDN/URL | Protocol | Port | Description |
|---|---|---|---|
| 2.debian.pool.ntp.org | UDP | 123 | Default NTP server (Default domain) |
| ttau.cs.txone.com | TCP | 443 | Component updates |
| apis.cs.txone.com | TCP | 443 | License activation for version 1.8.3 and later |
| storage.cs.txone.com | TCP | 443 | VDS pattern updates |
| odc.cs.txone-networks.com | TCP | 443 | License activation reserved for version 1.7.0 or older |
| https://help.txone.com/docs/elementone | TCP | 443 | Online help |
| https://www.txone.com/legal/license-agreements/ | TCP | 443 | EULA page |
| https://www.txone.com/privacy-policy/ | TCP | 443 | Privacy Policy page |
Version : 1.20.0 and later
| FQDN/URL | Protocol | Port | Description |
|---|---|---|---|
| 2.debian.pool.ntp.org | UDP | 123 | Default NTP server (Default domain) |
| apis.cs.txone.com | TCP | 443 | License activation for version 1.8.3 and later |
| storage.cs.txone.com | TCP | 443 | Component updates , VDS pattern updates |
| odc.cs.txone-networks.com | TCP | 443 | License activation reserved for version 1.7.0 or older |
| https://help.txone.com/docs/elementone | TCP | 443 | Online help |
| https://www.txone.com/legal/license-agreements/ | TCP | 443 | EULA page |
| https://www.txone.com/privacy-policy/ | TCP | 443 | Privacy Policy page |
9. PI Standard and Pro product package specifications
- PI Standard:
o Package dimensions: 115 x 79 x 17 mm (4.52 x 3.11 x 0.66 in).
o Weight: 27 g (0.95 oz). - PI Pro:
o Package dimensions: 109 x 62 x 26 mm (4.29 x 2.44 x 1.02 in).
o Weight: 75.9 g (2.68 oz).
10. Do you have any data on the impact scanning with PI would have on PC performance?
While scanning, the CPU usage ~30%, memory usage: 40~60MB on a PC.
11. What is the maximum amount of scan logs and asset information that can be collected by PI?
It depends on if it contains quarantined files or not; in general, more than 10K Scan logs and Asset Info can be stored in a Scanning Tool.
12. How does "CVE detection" work?
PI supports detecting CVEs that utilized specific malicious files for exploitation.
13. Why does Portable Security need administrator privileges?
- To scan whole systems
- The low-level APIs in the PS and PI require admin privileges to access the hidden partition in the PS and PI sticks for quarantining malicious files, as well as the write-protected partition for writing logs.
There are two workarounds:
- Pre-configure the admin credentials to the scanning tool configuration settings.
- Without administrator privileges, scanning the system via a Rescue Disk, which boots the system from PS and PI, is possible. However, this method requires rebooting the system (and changing the BIOS to boot from PS and PI), and its feasibility is hardware-dependent; some systems with encryption may not be supported.
14. How can I sync Linux logs to ElementOne?
You’ll need to sync logs from the Windows platform which can be triggered by pressing the ‘Sync’ button in the Scanning Tool.
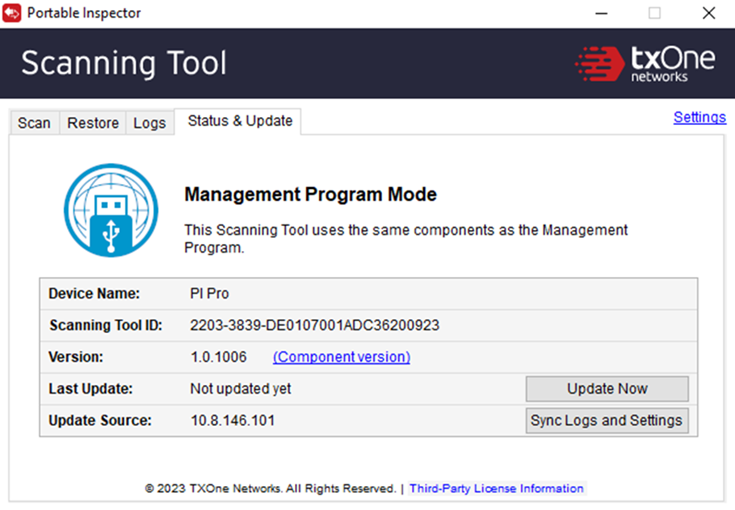
15. How can I remotely update the Scanning Tool license with ElementOne?
There are 3 ways to update the license (choose one):
- Click “Register” to re-register
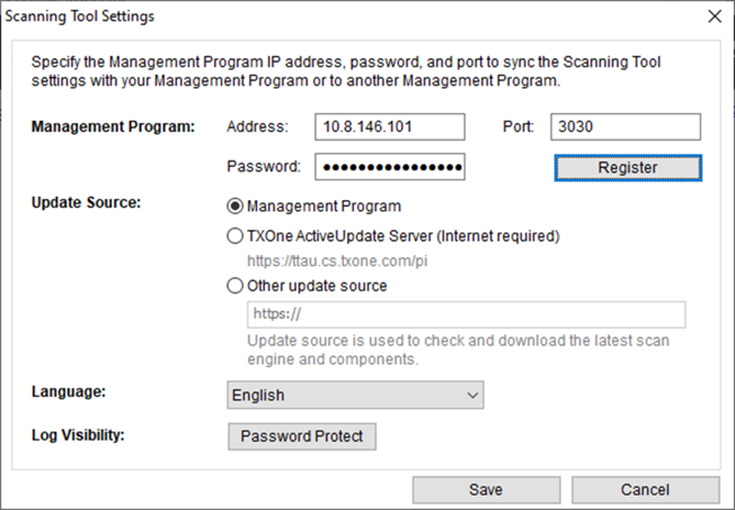
- Click “Update Now”
- Click “Sync Logs and Settings”
Configuration
1. How can PI be used in an environment that is under the GPO USB restriction policy?
- Navigate to Policy > Computer Configuration > Administrative Templates > System > Device Installation > Device Installation Restriction. Use the following policies with their specific configurations:
- Allow installation of devices that match any of these device IDs:
| Portable Inspector Pro | USB\VID_2203&PID_3839 USB\VID_2203&PID_E839 USBSTOR\DiskTXONE___PI_DISK_________ |
| Portable Inspector | USB\VID_2203&PID_3838 USBSTOR\DiskTXONE___PI_DISK_________ |
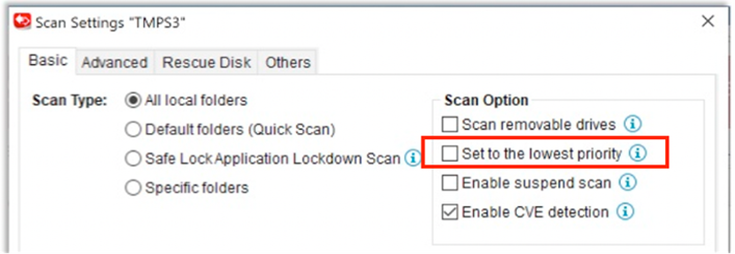
2. Is it safe to conduct the scan using PI on equipment that is online?
We encourage users to conduct the scan when the equipment is taken offline for maintenance. But if there are urgent circumstances that call for a scan while online, users may choose to enable "Set to lowest priority" in the scan option menu before launching the scan. However, enabling this option may increase the time needed to complete the scan.
3. How to reset PI to default factory settings
- Copy the “Support Tool” folder from the ST to the host, then you can reset your dongle.
- Execute the PISuprt.exe in the Support Tool.
- Go to the "More Tools" tab and choose Reset to Default Program Settings or Default Factory Settings.
4. How can I switch from Standalone mode to Managed mode?
The PI does not support directly switching between Standalone and Managed modes. The only way is to reset PI to the default factory settings and activate it again.
Troubleshooting
1. I received the error message, “Portable Security is not mounted properly, please follow the instructions and launch again”. What should I do?
Please refer to the knowledge base article , How to Fix Portable Inspector (PI) Device Mount Issues on the Linux Platform
2. The Portable Inspector binary files are detected as false positives by third-party antivirus software.
Portable Inspector employs a third-party application to protect its binaries. Consequently, some antivirus software may mistakenly flag these binary files as false positives. Builds up to version 1.0.1016 or earlier utilize this application. If these files are detected as malicious by third-party antivirus solutions, we recommend updating to Portable Inspector version 1.0.1018 or later and revalidating the binaries to resolve the issue.
3. The MS .NET Framework installer file is corrupted
The Safe Port scan result show “The file is corrupted“.
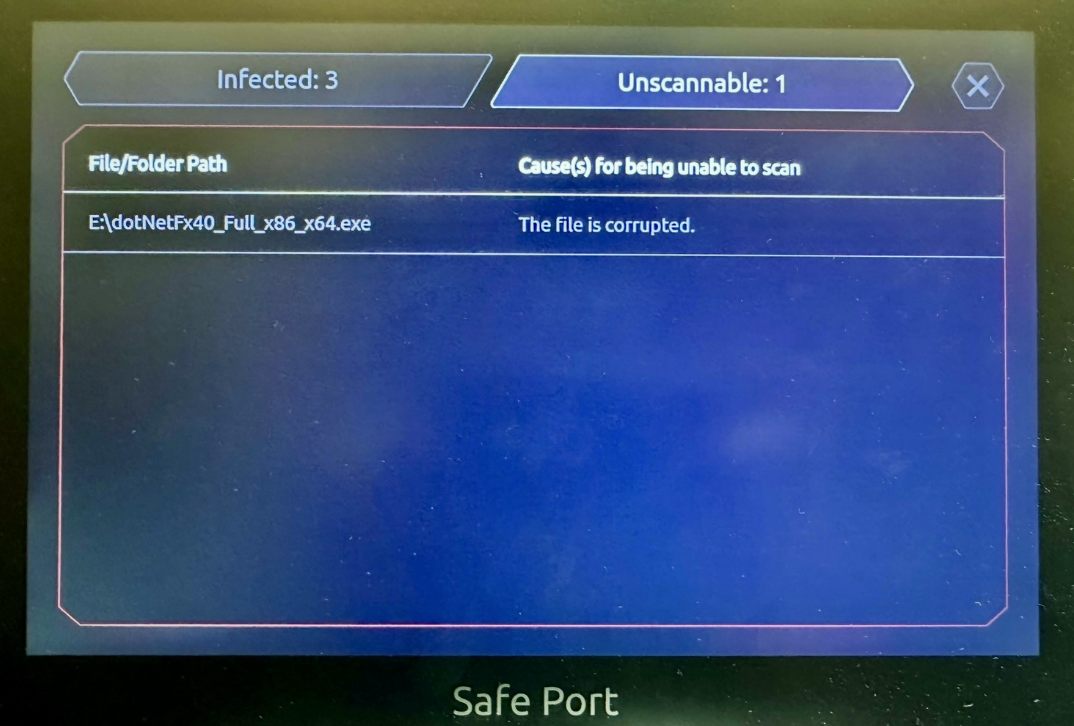
In certain versions of the .NET Framework installer, files with the extension .mzz are included. These files are identified as MS cabinet files but are actually proprietary file types modified by Microsoft, with no publicly available format. As a result, the scan engine cannot process these files, which may lead to the entire .NET Framework installer being flagged as 'The file is corrupt' in SafePort.
To resolve this issue, please add the files to the allow list to prevent false positives.
For support assistance, please contact us at support@txone.com or your Support Provider.

