Background
Retail is the most direct way for consumers and businesses to buy goods and services. Whether they are manufacturing, healthcare, food, or electronic products, enterprises ultimately sell their products through retail channels. Taking the United States as an example, consumer spending accounts for about 70% of the total economy, showing that industry is an essential part of the economic market [1]. Digital Transformation (DT) is one of the recent trends in retail industries to effectively sell products in 2022. Through the application of technologies such as big data, the Internet of Things, and artificial intelligence, it achieves not only effective operational efficiency and flexibility, but also provides personalized customer service for consumers [2][3].
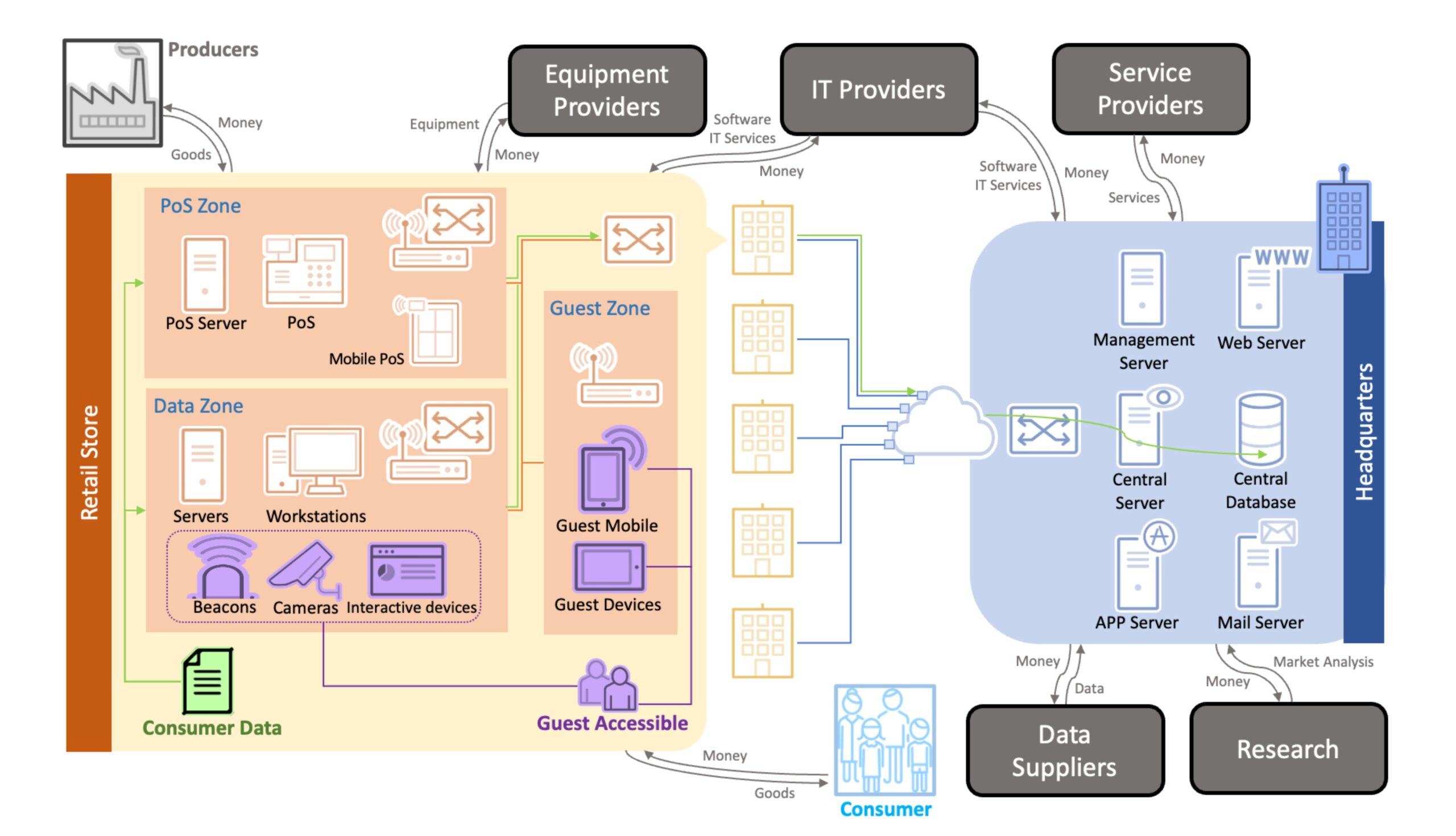
The consumer pattern of the retail industry involves the process from in-store or online production of goods to delivery to consumers. The type of In-store in figure 1 shows that a large-scale retail enterprise consists of a headquarters that supervises and manages the overall enterprise activities and multiple retail stores that provide customer-to-store services. As a retail store serving consumers directly, the connected network structure often includes:
a. Point of Sale (POS) Zone: Establishing customer purchase history, real-time inventory data, and intelligent order routing so that retailers can deliver the end-to-end experience customers expect.
b. Guest Zone: Providing wireless network services for consumers to measure traffic patterns and how many people are entering the store at a given time.
c. Data Zone: Collecting data from an application or connected device and incorporating analytical tools to understand customer habits and behaviors better.
Close partners of retail stores are, not only product manufacturers that provide merchandise for the retailer, but also infrastructure providers and IT service providers that build network services to enable in-store consumption or management. Meanwhile, any retail store will also provide in-store data to headquarters through the internet that they can analyze and subsequently adjust strategies according to the findings from this data. At headquarters, various IT equipment will be deployed according to the enterprise’s size. In addition to the server and database that can centrally process the in-store data collected by each retail store, it also includes mail servers that are used for communication or web servers that provide consumer browsing history among other things. Unlike the partners of retail stores, the headquarters often purchases data borne of market trend analyses from data suppliers or research institutions. They simultaneously outsource Service Providers to expand services in more markets due to the responsibility they bear to promote enterprise development and expansion of the market.
The storage and exchange of retail industry data includes: total transaction volume, transaction records, inventory status, and credit card information. In order to encourage customers to purchase their products repeatedly, the retail industry often conducts customer loyalty programs through membership systems or learns customer habits to provide customized services that invite consumers back. Suppose an enterprise suffers from a cybersecurity incident. It will no longer only impact basic operations, but also lead to the leakage of consumer data (including personal information, consumption records, behavior records, or credit card information), resulting in damage to corporate image, the need for colossal financial compensation, and even exposure of consumers to danger to their property or personal safety. One notable data breach incident in the retail industry is that of Target, where more than 70 million consumers had their data stolen, leading to a total loss of about 200 million US dollars in 2013. Home Depot also lost $179 million due to information leakage in 2014. In the above cases, we can see that the incidents were initiated by supplier chain attacks. Leveraging stolen credentials from retail suppliers to gain access privileges to the network, the hacker escalated privileges and moved laterally undetected until the hacker found the critical POS system. The malware downloaded the detailed information of credit cards on the POS system, and all the data was quietly exfiltrated to the attacker’s servers [4][5].
In addition to the consumer data voluntarily provided by consumers, their data can also encompass consumer activity, obtained from the POS system or behavior records collected through beacons, cameras, or other interactive networked devices, and finally stored in the server (shown in figure 1). However, consumer data will not be confined to a single retail store; its data will also be provided to headquarters through the internet for data integration and data analysis. This will allow other retail stores to read and write necessary content to provide consumers with services that aren’t restricted by location.
Threats Faced by the Retail Industry
The IT/OT equipment and cyber policies adopted by retail stores vary in each company’s own scale and marketing model. Implementing cybersecurity seems to be a massive challenge in many open and consumer data storage fields. For the sake of consumer data cybersecurity, the Payment Card Industry Security Standards Council has also formulated the PCI Data Security Standards (PCI DSS) and conducted on-site inspections by Qualified Security Assessors to ensure that industry-related units comply with PCI DSS cybersecurity requirements. Some US states even incorporate this standard into the law, which points to the importance of cybersecurity to the retail industry [6]. TXOne Networks analyzes the current situation of retail stores with headquarters, supply chains of retail, and in-store consumption patterns and finds the following potential threats:
1. The system is directly exposed to threats when a POS system’s network that has misconfigurations or unpatched endpoints and servers is in an open environment.
POSes have become the technology of choice for retail companies because of their convenience, which makes it easier for people to manage inventory, share customer data, and manage business. Although the application of Point-to-Point Encryption (P2PE) minimizes the impact of attackers [7], considering the characteristics of the POS system’s endpoints in an open geographical environment, attackers can still easily leverage connected electronic scales or equipment that are not used by staff to connect to POS servers. This would expose end devices and servers with misconfigurations or unpatched directly to cyber threats.
For example, SAP, one of the world’s largest suppliers of enterprise application software, has multiple high-risk vulnerabilities in its POS server [8]. Attackers only need to access the network interface of the POS system, and then they can execute any management function on the server they wish. Management functions such as accessing credit card information, tampering with commodity prices, and closing POS services.
For another example, Dixon’s Carphone unwittingly installed POS malware on over 5,000 terminal devices from July 2017 to April 2018 simply because the Windows OS running on their POS was not patched for known vulnerabilities [9]. In addition, since there can be many retail stores in one enterprise, it is difficult to ensure that all store personnel have enough cybersecurity awareness to set up secure configurations for endpoints of the POS system. Even if the store personnel had that awareness, some manufacturers do not allow personnel to change the default configurations [10]. In cases like these, adversaries can leverage default or easy-to-guess passwords to compromise POS systems without breaking a sweat.
2. IoT assets of retail applications are in an interactive or open environment, allowing cyber attacks such as data theft, hijacking, spoofing, and DoS to frequently occur.
Retail stores sometimes use IoT technology to collect consumer data or interact with consumers to increase customer traffic and sales to provide an immersive omnichannel experience. In the modern age of smart mobile devices, consumers can access a more intelligent shopping experience by installing store apps, which makes the network environment more complex. Let’s take beacon technology for example, one of the ways retail stores use technology to promote sales [11]. Its technology works by placing small hardware devices in stores that sense the surrounding mobile devices to provide consumers with benefits such as product search, notification of discounts, or inventory inquiries. The iBeacon communication protocol is the most common in beacon technology. Its sensor only transmits data such as Universal Identifier (UUID), Major Number, and Minor Number to identify context information such as enterprises, specific stores, and locations. However, suppose it cooperates with the consumer’s mobile phone app and obtains access rights. In that case, the retail store can collect customer data such as name, email, birthday, location, brand loyalty, and social network influence data [12][13][14] – this makes the cybersecurity of Beacon technology that much more critical. Since the beacon device is placed in an open environment, anyone can remove the device from the wall. In addition to changing the device’s settings through default or easy-to-guess passwords, researchers have also found that iBeacon is vulnerable to hijacking, spoofing, DoS, and other risks [15][16].
Though the risk of hijacking the content broadcast by beacon devices is not serious, if competitors maliciously use the same beacon data and design the same value for the App, consumers can instead be led to the competitor’s page when they pass the beacon in the retail store. [17].
Besides, with the consumers’ permission, the store app will send consumer data to the management server, which challenges the cybersecurity of the App and server. The ease with which this can be done was demonstrated in the iBeacon Scavenger Hunt in 2014. During this beacon technology event, the cybersecurity researchers won the cybersecurity competition before the event [18] because they reverse engineered the App and completed the attack quickly. Thus, attackers can also easily find the server network location to attack by the aforementioned method.
Unfortunately, other IoT assets similar to beacons also have similar risks.[19] Therefore, it is necessary to pay attention to the cybersecurity protection of the server. If the enterprise manages the server, it should only be able to execute trusted applications or websites and give each endpoint device minimal interaction authorizations. The server hosted by a third party should also evaluate its cybersecurity practices.
3. Significant growth in ransomware attacks in the retail industry, resulting in numerous retail stores shutting down.
According to TXOne Threat Research, LockBit 2.0 launched a high proportion of ransomware attacks in early 2022, and their cyber attacks on the retail industry in particular has increased significantly [20]. We don’t have to flashback very far to find examples of these. As recently as April 2022, the Works had to temporarily shut down all 526 stores due to servers being hacked [21]. When the Kaseya VSA remote management service was hacked by bad actors associated with REvil in June 2021, one of the many companies that were compromised was the Swedish Coop Grocery Store, which had to temporarily close about half of its 800 stores [22][23].
Because retail stores are connected to their headquarters’ network, and related services are interlocked with each other, any location in the business must be protected against ransomware attacks. In the case of headquarters, except for the vulnerabilities of external service, the work content of employees includes the following:
a. Dealing with retail store problems or seeking better market opportunities through external cooperation.
b. The processing of very diverse email sources.
c. Submitting data queries or analysis requirements.
These employees are often connected to the enterprise’s internal server, providing an opportunity for ransomware execution and proliferation. In the Coop Grocery Store incident, many retail stores stopped running POS, locked down by ransomware due to the software vulnerabilities hosted by third parties. This case indicates the importance of hardening security assets. Ideally, even if the assets were accidentally installed with ransomware, the ransomware would not work.
4. Intentional or unintentional abuse of consumer data by headquarters insiders, making data leakage difficult to prevent.
While the retail industry is less costly than other key industries, its average cost has risen sharply since 2020, to the point where it is only below media, healthcare, and public sectors [24]. In addition to hacker attacks, data leakage often happens, intentionally or unintentionally by insiders [25]. Since retail companies have different cultures and regulations, it is easy for some internal employees who lack security awareness to cause leaks by accidents. They may check the shopping or behavior records of celebrities based on their curiosity, and innocently share them with their friends, resulting in a leak. Alternatively, internal analyses are based on market analysis needs, and there is no good API design within the enterprise so that analysts can capture identified customers’ data on personal computers. Data leakage can also occur when analysts’ personal computers are connected to insecure networks, run programs from unknown sources, or share equipment with others. In these cases, enterprises should conduct cybersecurity awareness training for internal personnel and deploy appropriate cybersecurity management. For further details, please refer to the summary and mitigation chapter below [26].
How to Mitigate Potential Threats to Protect Retail Industry?
In the retail industry, to protect the data of payment card holders, the Payment Card Industry Security Standards Council has also formulated the PCI DSS Standards for any organization involved in storing, transmitting, or processing cardholder data. PCI DSS specifies 12 requirements [6] that mitigate the risk of a retail store or vendor getting cardholder data into the hands of attackers. We recommend referring to the PCI DSS regulations. We also recommend that the retail industry deploy network segmentation, harden security on critical servers, implement zero-trust access, and educate employees with cybersecurity awareness:
a. Segment the retail network so that the POS Zone, Data Zone, and Guest Zone can be independent of each other. When a specific area is attacked by ransomware, the software can be quickly blocked in a specific area without continuing to spread.
b. Harden critical servers so that devices with consumer data can only run trusted applications and websites. That way, even if ransomware is embedded, it cannot run as well.
c. Implement zero-trust access, restricting the minimum interaction rights of each endpoint device, allowing attackers to perform only limited actions even in an open environment.
d. Provide employees with proper cybersecurity training. In addition to mitigating the risk of data leakage, it can also reduce the risk of employees’ actions resulting in ransomware incidents.
When retail stores are widely distributed, we suggest that a central visualization management console be established so that the entire enterprise can manage information such as online logs, events, and lifecycle equipment in each store. This console can also quickly analyze the root cause of an attack and respond to incidents so that the attack does not continue to spread.
References:
[1] Will Kenton, “Core Retail Sales”, Investopedia, Feb 19 2022, Accessed July 4 2022
[2] Deloitte, “Retail Trends 2022”, Deloitte, Accessed July 4 2022
[3] Oro Team, “What is Digital Transformation in the Retail Sector? Key Drivers, Trends, and Examples”, Oro Inc, Mar 23 2022, Accessed July 4 2022
[4] Corrin Jones, “WARNINGS (& LESSONS) OF THE 2013 TARGET DATA BREACH”, Red River, Oct 26 2021, Accessed July 4 2022
[5] ArcTitan, “Case Study: Home Depot Data Breach Cost $179 Million”, ArcTitan, Aug 20 2021, Accessed July 4 2022
[6] IT Governance USA Inc., “PCI DSS: Are you taking payment security seriously?”, IT Governance USA Inc., Accessed July 4 2022
[7] Saravana Kumar Rajiah, “The Security Vulnerabilities of PoS Systems and How to Address Them”, Encora, July 16 2020, Accessed July 4 2022
[8] SAP Product Security Response Team, “SAP Security Patch Day”, SAP, July 11 2017, Accessed July 4 2022
[9] Danny Palmer, “My stolen credit card details were used 4,500 miles away. I tried to find out how it happened”, ZDNet, Sep 16 2020, Accessed July 5 2022
[10] Aleksei Stennikov, Timur Yunusov, “POSWorld: Vulnerabilities within Ingenico Telium 2 and Verifone VX and MX series Point of Sales terminals”, Black Hat Europe 2020, Dec 10 2020, Accessed July 4 2022
[11] AGADIR-GROUP, “7 Beacon Technology Retail Tips to Boost Sales in 2022”, AGADIR-GROUP, Accessed July 4 2022
[12] Oksana Bespalova, “iBeacon Technologies and Bluetooth Low Energy For Retail”, Navigine, Apr 10 2017, Accessed July 4 2022
[13] Devika Girish, “6 Myths around Beacon Security and Privacy”, Beaconstac, Jan 5 2022, Accessed July 4 2022
[14] H.O. Maycotte, “What Data Can a Beacon Actually Collect?”, Multichannel Merchant, Apr 9 2018, Accessed July 4 2022
[15] Trevor Longino, “3 Beacon Security Issues You Should Consider”, Kisi, Aug 9 2018, Accessed July 4 2022
[16] Hui Jun Tay, Jiaqi Tan, Priya Narasimhan, “A Survey of Security Vulnerabilities in Bluetooth Low Energy Beacons”, Carnegie Mellon University, Nov 2016, Accessed July 4 2022
[17] Andrew Levi, “Should We Be Worried About Beacons Being Hacked?”, Total Retail, May 23 2016, Accessed July 4 2022
[18] Alasdair Allan, Sandeep Mistry, “Hacking the CES Scavenger Hunt”, Make Magazine, Jan 3 2014, Accessed July 4 2022
[19] i-SCOOP, “The Internet of Things in the retail industry – applications and use cases”, i-SCOOP, Accessed July 4 2022
[20] Hank Chen, Mars Cheng, “Safeguarding OT environments against the LockBit 2.0 ransomware”, TXOne Networks, May 25 2022, Accessed Jun 28 2022
[21] Naveen Goud, “Ransomware attack on The Works stores of UK”, Cybersecurity Insiders, Accessed July 4 2022
[22] Joe Tidy, “Swedish Coop supermarkets shut due to US ransomware cyber-attack”, BBC News, July 3 2021, Accessed July 4 2022
[23] DAN GOODIN, “Up to 1,500 businesses infected in one of the worst ransomware attacks ever”, Ars Technica, July 7 2021, Accessed July 4 2022
[24] IBM Security, “Cost of a Data Breach Report 2021”, IBM, July 2021, Accessed July 4 2022
[25] Trend Micro, “Data Breach”, Trend Micro, Accessed July 4 2022
[26] Mars Cheng, Yenting Lee, Max Farrell, “ICS Giants of the Fortune 500: The Frequency and Risk of Data Exposure”, TXOne Networks, Dec 2 2021, Accessed July 4 2022