Background
The pharmaceutical industry is highly globalized. Its product research and development costs are high, time-consuming, and risky. Furthermore, the research and development outcomes are protected by patents for a long time, making their intellectual property a coveted target for adversaries. An overview of the pharmaceutical industry ecosystem is shown in Figure 1.
First, the industry’s goal is to provide patients with medicine. When new medication needs to be developed, its medicine development mainly includes discovery, preclinical research, clinical development, review, and monitoring. In the discovery stage, there are a few phases. First, the researchers of the pharmaceutical company will carry out a series of identification and verification procedures to find the genes and proteins that play an important role in disease treatment. This is followed by the screening and optimization of the compounds. In the last phase of the discovery stage, they find the biologically active pharmaceutical ingredients (APIs) that produce results with the expected efficacy. The next stage, preclinical research, is where the researcher will conduct preclinical research in vivo to ensure the medicine is safe. In the clinical development stage, the medication will be tested through clinical experiments and volunteer research and continually adjusted accordingly for safety and efficacy.
Take America, for example. There, the new medication will be reviewed by the U.S. Food and Drug Administration (FDA) after clinical development. If the review results in approval, pharmaceutical companies are still required by the FDA to use the FDA Adverse Event Reporting System (FAERS) to monitor drugs and continuously implement post-marketing safety supervision. Taking vaccine manufacturing as an example, when the FDA approves a drug, a pharmaceutical company’s factory can manufacture API products from raw materials and various compounds and mix them with other chemical ingredients to convert the medicinal substance into a bottle or syringe suitable for use in vaccinations. Next, medicines will be shipped to countries around the world, using pharmaceutical logistics, under strict supervision and temperature control and distributed to local healthcare providers in accordance with local government policies, before they are finally provided to the patients that need them[1][2][3][4].
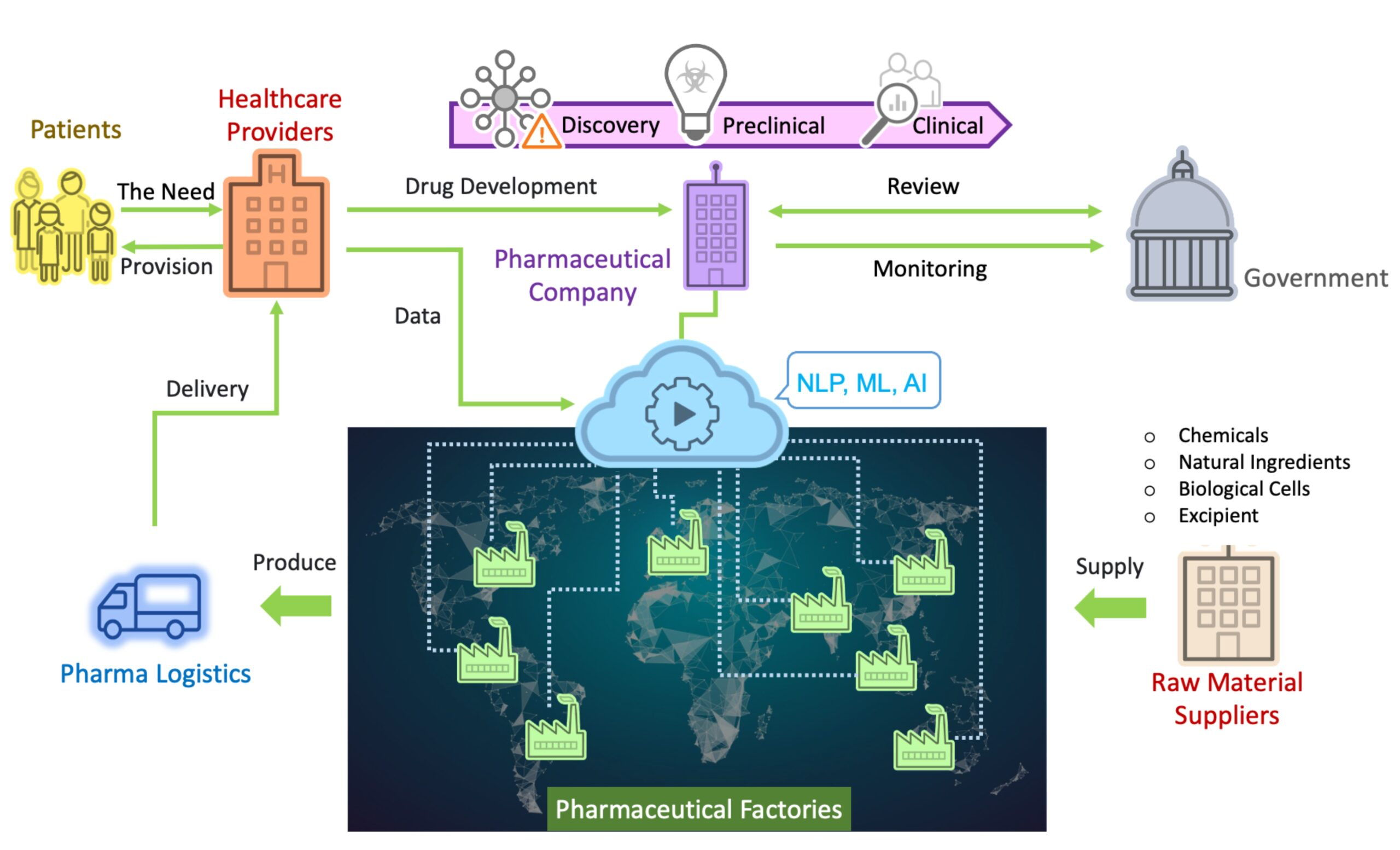
As shown in Figure 1, the factories of pharmaceutical companies are the most direct source of medicine supply. When the factories are damaged, patients will not be able to obtain medications immediately, which may cause irreversible consequences. Thus, this article will explain the factory trends and current situation of pharmaceutical companies, thereby revealing their potential security threats:
• Introducing factory automation: Larger pharmaceutical companies have been looking for solutions to automate their factories in recent years to achieve higher manufacturing efficiency and reduce operating costs. For example, factories can use machine learning technology to combine data from healthcare providers to produce personalized medicines for patients. Another example is the use of Native Language Progressing (NLP) technology to help factories analyze multiple data sources for industry forecasting, allowing factories to predictively produce medicines accurately [5][6]. Pharmaceutical companies such as Merck, Pfizer and Sanofi have already embarked on the road of Pharma 4.0. For more information, please refer to the appendix [7].
• Application of continuous manufacturing technology: Given the benefits of improving medicine quality and reducing medicine shortages, more and more factories are gradually transforming from traditional batch manufacturing to continuous manufacturing under the FDA’s promotion. Continuous manufacturing is a method of manufacturing where the processes are linked together so that factories can supply raw materials and produce medicinal products without interruption.
• Compliance with pharmaceutical regulations: Since medicines directly affect human health, governments worldwide have strict requirements for developing and manufacturing medicines. In addition to complying with the regulations of organizations such as the FDA, EMA, GMP, or GAMP, factories must avoid asset warranty failures in the factory, and asset owners cannot install third-party software for asset management, which makes regulatory compliance more complicated. Therefore, it will improve the compliance efficiency of the factory to provide a visual management component of the pharmaceutical factory through free installation [10].
Threats Faced by the Pharmaceutical Industry
Based on the severe impact of the pandemic in recent years, it has been found that when the production or distribution process of medicines is disrupted, people will not be able to obtain medicines immediately, causing panic among people and even irreversible bodily harm. Based on the above considerations, TXOne Networks analyzed the factories and logistics of pharmaceutical manufacturers and identified the following potential threats:
1. The machinery and systems in the pharmaceutical factory are connected to the internet, providing adversaries with more attack vectors under the trend of factory automation
To improve the manufacturing efficiency of medicines and reduce the operating costs of factories, pharmaceutical companies have gradually introduced automated factories and connected many machines and systems to the network. For example, Merck Pharmaceuticals has established factories with various modules and connected the factories through the network to flexibly produce different types of medicines to meet the rapid production of small batches of medicines. Another case is Sanofi Pharmaceuticals, a company that connects sensor data in its factories to the Internet and provides managers with real-time operational information through digital twin technology. In addition, they also use Collaborative Robots (Cobots), Augmented Reality (AR), and other technologies to achieve higher execution efficiency [7].
When factories connect many machines and systems to the network, attackers will have more opportunities to perform initial attacks on factories through technologies such as Internet accessible devices or wireless compromise. In particular, the use of industrial communication protocols that lack security by design makes the vulnerability of the communication protocols more vulnerable to hackers, such as PROFINET, PROFIBUS, Ethernet/IP, and Modbus. In addition, the security risks of industrial robots, augmented reality, and additive manufacturing used in automated factories will also pose potential threats to the factory. Please refer to [11] for detailed automated factory threats.
2. Due to acquisition and outsourcing strategies, the network infrastructure of the factory is made more complex, and hackers can potentially use compromised trusted devices to enter the intranet
To achieve higher R&D capabilities, expand product therapeutic domain, and expand production scale, acquisition and outsourcing are common strategies for pharmaceutical companies. In the first half of 2022, the market value of mergers and acquisitions (M&A) in the medical and pharmaceutical industries reached USD$4.32 billion, which is more than two times the value generated within the same span of time last year [12]. In M&A activity, it is easy to integrate legacy and new assets into the same IT network simultaneously, allowing legacy IT assets that are vulnerable to cyberattacks access to the corporate network. This means that the legacy asset can provide an entry point to the corporate network once it has been compromised. Besides the trend toward increasingly networked machinery and systems in factories, these generally considered trusted sources of corporate networking are also bringing threats into the OT environment.
There is a similar trend in outsourcing activities. The global biotech and pharmaceutical services outsourcing market was valued at USD$66 billion in 2021, and it is expected to expand at a CAGR of 5.5% from 2022 to 2030[13]. To enable customers to check current progress and status in real-time, pharmaceutical factories will eventually provide remote services for customers to connect to, which would permit more unmanageable sources to connect to the OT environment.
3. Continuous manufacturing enables pharmaceutical factories to use more sophisticated equipment, and any minor interruption will result in severe losses in the production process
Driven by the FDA, more and more pharmaceutical factories are adopting continuous manufacturing to improve medicine products. Continuous manufacturing, however, relies heavily on automated machinery, which is often customized to produce a specific product. The complexity and sophistication of such machinery means that any minor interruption to the equipment will result in defects in the production process and cause factory damage in the form of operational standstill or economic loss [14]. Because most continuous manufacturing equipment is designed with precision and does not allow third-party changes, it is difficult for equipment owners to deploy adequate cybersecurity protection. Meanwhile, in an environment that does not allow any minor equipment disruption, factories need to prevent cyberattacks from outside the equipment so that the factory can continue to operate.
4. During the delivery of medicines, the IoT devices are embedded in the GPS tracking and status monitoring of medicines; if the signal is hijacked, the devices will run the risk of information confusion or delayed shipment:
Medicines with high demand face storage and transportation challenges after production. For example, a medicine might be manufactured in Belgium and then must be stored at minus 70 degrees Celsius and shipped globally. In order to avoid medicine theft or other illegal actions during the transportation process, one of the solutions for shipping medicine to factories is to use IoT devices with GPS tracking and situation monitoring. In this way, medicine buyers can track the environmental changes of medicine, and if the medicine is lost or damaged during transportation, factories can immediately send new medicine to reduce harm to buyers [15].
Before the medicine is manufactured and provided to healthcare providers, the medicine’s pipeline includes medicine manufacturers, pharmaceutical logistics suppliers, and government purchasers and distributors. Attackers can hijack and forge GPS signals through radio frequency (RF) tools so that trackers (such as government buyers and distributors) can get the wrong medicine information. In addition to affecting the shipping schedule, if the country’s people urgently need medicines, wrong information can also put the country in a turbulent situation.
How to Mitigate Potential Threats
The factories of pharmaceutical companies need to comply with the regulations of organizations such as the FDA, EMA, GMP, or GAMP. They also need to defend themselves against the threats mentioned above. In order to achieve both these goals, TXOne Networks recommends the following OT zero trust-based solutions to mitigate potential threats that factories may encounter:
1) Security inspection: Taking the form of a USB flash drive, the portable scanning device can scan and clean assets of malware without needing to install software. Leveraging the portable security scanning tool allows pharmaceutical companies to both detect malware without altering sophisticated manufacturing equipment and avoid warranty violations. This will help the pharmaceutical industry to ensure the integrity of the device while complying with the regulations of the pharmaceutical industry, such as the FDA’s CFR Title 21 Part 11:
- Reduce the impact of third-party software on the medicine production equipment or violate the equipment vendor’s warranty terms.
- Even if the production line of the pharmaceutical factory is in an air-gapped environment, Trend Micro Portable Security™ 3 can still assist in malware scanning with offline scanning.
- Quickly inspect whether there is malware in the electronic equipment of personnel and suppliers; perform any needed cleanup or quarantine automatically.
- The asset information collected during each scan is recorded and sent to the central management console for review and archiving.
- Asset information and malware scan results are transmitted using AES-256 hardware encryption, and the transmission process is also automatically checked for malware to protect files and ensure data integrity.
2) Network defense: OT network defense can leverage network segmentation, network access control, virtual patches, and better intrusion detection analysis to prevent vulnerable assets from turning into large-scale disasters. It also simplifies monitoring and makes it more difficult for hackers to gather information or make lateral movements within the OT network. We recommend deploying the OT network as follows:
- Network segmentation: Network segmentation can be further divided into internal segmentation and micro-s Internal segmentation applies to dividing up a large scale or area based on the available technology, bandwidth, and communication protocol. Similarly, micro-segmentation refers to technical solutions that allow the user to reduce the scope or area to be protected to a smaller scale or even to individual assets. This enables industrial network visibility as well ICS protocol filtering of devices on the network without the need for changing the existing network architecture. This way, it does not interfere with the existing configuration.
- Virtual patching technology: This is implemented through a host-based intrusion prevention system, also known as a network IPS. These devices have specially designed network policies for packet filtering. These are specifically designed to defend against attacks that exploit known vulnerabilities without forcing endpoints to perform security updates, which means it can avoid system restarts and production line downtime.
- Network trust listing: Supports in-depth analysis of various industrial control network protocols and L2-L7 network traffic, provides protocol command editing and endpoint connection allow list operations, and establishes network rule allow lists. In addition, with network segmentation, all hardware protection devices can be visually monitored and managed through the central control platform. This will also reduce risks by implementing the concept of least privilege.
3) Complete visibility in OT environments: Pharmaceutical factories connect many machines and systems to the network, providing attackers with more initial access techniques such as Internet Accessible Device or wireless compromise. At this moment, the factory security team needs a clear and visible platform to manage the information security of many devices in real-time so that when an attack occurs, managers can immediately detect and deal with it. OT Defense Console™ gives the cybersecurity manager of pharmaceutical factories a comprehensive, consolidated overview. OT Defense Console™ is also organized into alerts, assets, and incident events, allowing the cybersecurity team to directly monitor the security of their enterprise’s industrial control system.
References:
[1] Tuba Khan, “COVID-19 Vaccine Distribution the Next Supply Chain Frontier”, PharmaShots, Aug 13 2020, Accessed Aug 17 2022
[2] Katsura Chemical, “What is an API?”, Katsura Chemical, Accessed Aug 17 2022
[3] Anindya Ghosh Roy, “What are drug substance and drug product?”, Lösungsfabrik, May 24 2018, Accessed Aug 17 2022
[4] Abhay Pandey, “Overview Of All Phases In Drug Development And Discovery Process”, NorthEast BioLab, Accessed Sep 4 2022
[5] The Keenfolks, “Top 5 Pharmaceutical Industry Trends and Predictions for 2022”, The Keenfolks, Accessed Aug 17 2022
[6] Igor Kruglyak, “Pharma will innovate and prosper further: Top 10 pharmaceutical industry trends in 2022”, Avenga, May 18 2022, Accessed Aug 17 2022
[7] Tim Sandle, “Pharmaceutical sector embracing Industry 4.0”, Digital Journal, Sep 22 2018, Accessed Aug 17 2022
[8] Shane McLaughlin, “Continuous Manufacturing vs Batch Manufacturing in the Pharmaceutical Industry”, SL Controls, Accessed Aug 17 2022
[9] Pfizer 2019 Annual review, “Portable. Continuous. Miniature. Modular.”, Pfizer, Accessed Aug 17 2022
[10] Michael Cheng, Max Farrell, “Best Practices for Pharmaceutical Manufacturers: Trend Micro Portable Security™ 3”, TXOne Networks, Sep 9 2021, Accessed Aug 17 2022
[11] TXOne Networks Blog, “Potential Threats to Automated Factory”, TXOne Networks, Aug 24, 2022
[12] LiveMint News, “M&A deal value in healthcare, pharma hits record high in first half of 2022”, LiveMint, Jul 12 2022, Accessed Aug 17 2022
[13] Grand View Research, “Biotechnology & Pharmaceutical Services Outsourcing Market Report, 2030”, Grand View Research, Accessed Aug 17 2022
[14] Dan Brettler, “Evolving risks in continuous manufacturing”, Swedish Institute of Computer Science”, Pharma Manufacturing, Oct 28 2019, Accessed Aug 17 2022
[15] MYTRACKINGDEVICES™, “Use Case: GPS Tracking & Condition Monitoring of the Pfizer Covid-19 Coronavirus Vaccine”, MYTRACKINGDEVICES™, Nov 20 2020, Accessed Aug 17 2022