Background
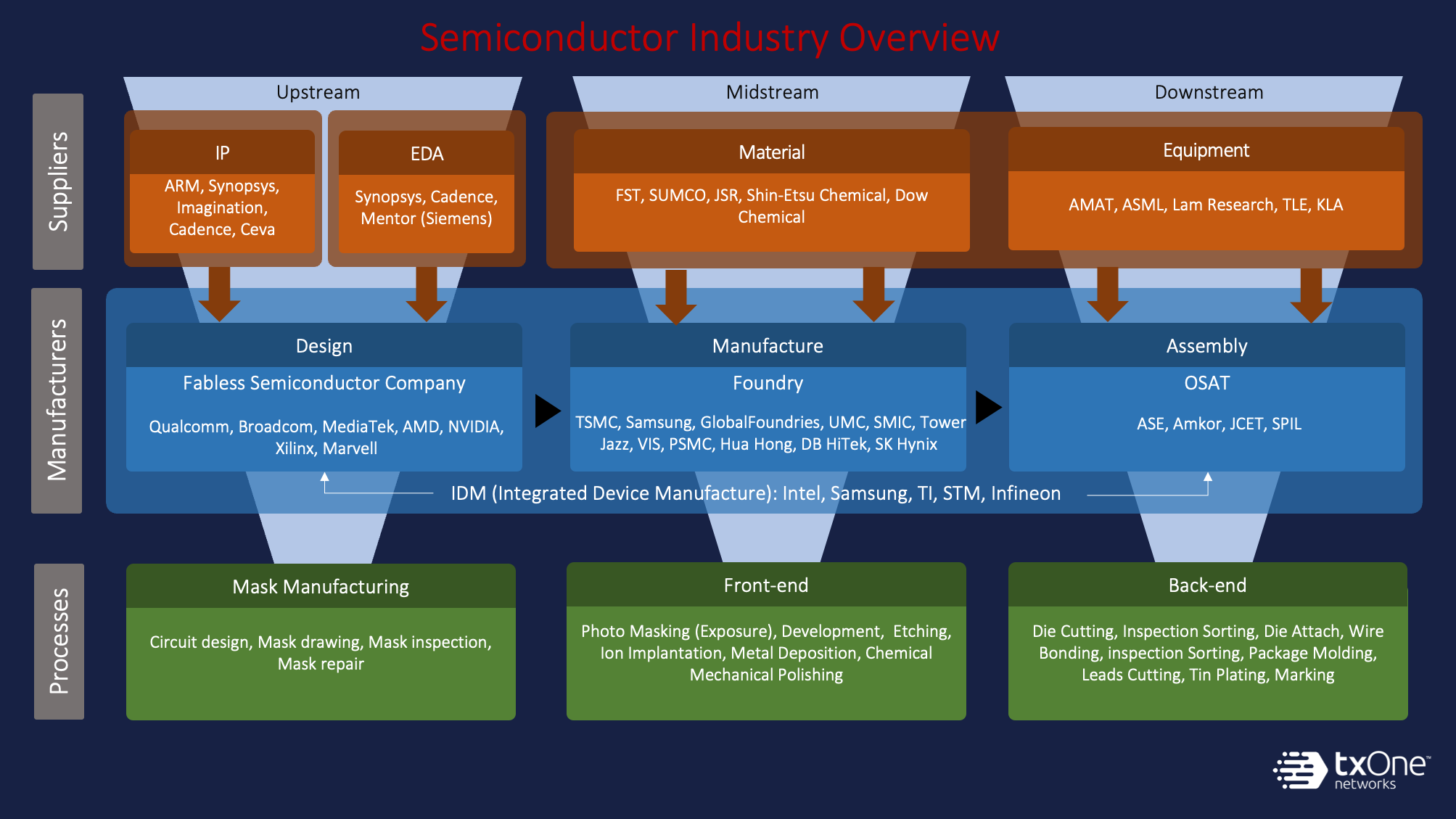
With the surge in demand in the global electronic market (PC, multimedia, networking, and communication devices), global semiconductor market revenue has been pushed to a new peak. The semiconductor industry’s supply chain is highly specialized to support the vertical’s unique needs. As a result of this specialization, the industry’s value chain is broken into “upstream”, “midstream”, and “downstream”. The value chain begins from so-called “upstream” industries, including integrated circuit (IC) design, and layout. “Midstream” refers to IC manufacturing (also known as wafer fabrication and processing, which is the most capital and technology intensive). Finally, “downstream” refers to integrated circuit (IC) packaging and performance testing. Surrounding industries, such as PCB modules and board assembly, are required to complete the final product.
Due to industrial specialization in semiconductors, companies focus on different markets following their customers’ product requirements. For example, IC design companies such as Qualcomm, Broadcom, MediaTek, etc., will choose suitable intellectual property (IP) or electronic design automation (EDA) tools according to different product development needs. Wafer fabrication and assembly vendors will choose the appropriate semiconductor materials and equipment suppliers for better process control. Well-known representative companies include TSMC, Samsung, GlobalFoundries, ASE, Amkor, and others.
To reduce impact on the availability or integrity of critical manufacturing by epidemics, cyber attacks, or terrorism, U.S. President Biden called for a review of America’s supply chains for semiconductors in 2021 [1]. Thus, the semiconductor industry should fully understand the threats that come from suppliers, equipment manufacturers, and partners in the ecosystem to ensure that they are ready for future risks.
Threats Facing by Semiconductor Manufacturers
Since each production activity in the semiconductor industry must invest huge capital to purchase many critical assets such as process, metrology, and material handling equipment, it also includes the servers and controllers required by the equipment. For example, a 300mm wafer fabrication requires at least US$2 billion in capital expenditure and US$700 million in operating expenditure. A single photolithography stepper costs more than US$100 million to manufacture – a process of equipment production which takes at least 15 months to complete – and it is only one of the many pieces of equipment required by the semiconductor manufacturing process [2][3].
At the same time, because of industrial specialization necessary in semiconductor production, one company cannot easily be replaced by another. When one company experiences a ransomware attack, it may interrupt a specific production line and even affect the entire electronics industry. Because of this close cooperation between upstream and downstream organizations of the semiconductor industry, it is challenging to ensure cybersecurity only by protecting our own factories – we also need to respond to the risks of supply chain attacks.
To focus on the scope of discussion, TXOne Networks analyzed the current situation and supply chain of enterprises in the core of the semiconductor industry, wafer fabrication and its upstream and downstream product design and back-end process stages, and found the following potential threats:
1. Installation of Unauthorized or Unknown EDA Tools for Cost-Benefit Considerations
In the IC design stage, due to the high price of EDA software, small and medium-sized businesses (SMBs) cannot afford a set of development software packages for each IC designer. Therefore, SMBs often have only one set of EDA software installed on servers for IC designers to use together with remote connections. However, some interns or engineers without access right to the server may use school teaching schemes or try to install unidentified EDA software on their personal computers to learn design skills. In this case, if trusted personnel bring their computer into the IT or OT network without valid the device of integrity, the company will face cybersecurity risks.
The demand for working from home has increased after 2020, thus the IC design company does not require personnel to work on site, the engineer can use VPN connection mechanism which provides attackers with more attack vectors. For example, Cadence, a specializing in producing EDA software for designing ICs, systems on chips (SoCs) and printed circuit boards, suffers from Log4j vulnerability impact in 2021 [4]. Therefore, in network environments that cannot be completely isolated, proper vulnerability management is required. It is enough to show that in the network environment that cannot be completely isolated, enterprise software servers need to do proper vulnerability management.
In addition, due to the high price of critical assets, small- and medium-sized IC design companies may not be able to purchase the equipment required for development, processing, or testing so they will outsource part of their business to other manufacturers. For example, IC design companies with more limited capital will outsource their packaging and test work to semiconductor assembly and test (OSAT) factories to maximize benefits and perform final tests on their wafers to ensure that the products meet customer needs.
In this case, the personnel of the semiconductor packaging and testing factory set up the test environment and directly provide remote connection service to equipment for remote operation. Some semiconductor test equipment is “legacy”, or over 10 years old. This gives attackers more opportunities to exploit the legacy equipment’s high-risk vulnerabilities. More seriously, to improve the efficiency of semiconductor packaging and testing factories, much equipment will be connected to each other and share testing software. Therefore, when one asset is under attack it may affect all connected production line equipment.
2. Dangerous Remote Connection for Fab Equipment Maintenance
Regardless of the semiconductor front-end processes or back-end processes stage, most of the critical assets used are precisely designed and cannot allow the owner to use any program to make changes. This makes it impossible to directly deploy assets on equipment in terms of information security protection. Security software also makes it difficult for general IT information security solutions to be applied in the OT environment.
When the equipment needs to be repaired or troubleshot, the assistance of the equipment manufacturer is necessary. To enable equipment manufacturers to understand problems quickly, some manufacturers will use the remote service method of opening assets for management. If the attacker can obtain the tokens needed to connect at this stage, this will affect the entire OT environment. The world’s largest semiconductor equipment manufacturer ASML has also reported incidents such as attempted attacks or data theft [5][6]. In addition, device makers have sophisticated and high-tech products and hold the critical knowhow to the world’s advanced chip manufacturing processes, making them easier targets for state-sponsored hacking groups.
3. APT Attacks Triggered by Insider Threat
The semiconductor industry began to globalize in the 1980s, and its role in products and operations is vital to leaders across industries in the global economy. For example, since chip assembly and the final testing process both require much labor, many European and American companies established factories in Southeast Asia and Eastern Europe early on to get access to low-cost manufacturing locations and support from local governments [3]. Generally, the bigger the company, the more difficult it is to manage employees’ confidential information. Advanced Persistent Threat (APT) attacks sometimes happen when employees with confidential information are convinced or manipulated to further a cyber incident.
4. Weak Security Controls and Governance in Hyper-Connected Production
Most IC foundries will provide remote access servers to their outsourced foundries partners so that bilateral teams can keep the instant status of the process progress, winning more customers’ trust. In this scenario, the network between foundries requires that the interconnected production facilities operate as a single virtual plant. If any company fails to do appropriate cybersecurity technical control and governance, it may expose the foundry to risks and even affect the stability of the supply chain.
5. Much Equipment Still Lacks a Central, Visual Platform to Manage Log Events and Vulnerabilities
In a 300mm Wafer Fabrication, there are approximately 250 to 300 critical assets with 8,000 to 15,000 endpoint devices.[2] Such a large and unpatched environment can easily become a breeding ground for malware. Engineers need a centralized and visual management platform to detect it at an early stage and manage a large number of devices. In addition, many critical assets are too sophisticated, and engineers cannot understand the actual software composition of the assets. Thus, except for recording network and system log events, they should also understand the Software Bill of Materials (SBOM) [7] of the assets, so that asset owners can quickly respond to newly discovered vulnerabilities and execute the organization’s mitigation plan accordingly.
How to Mitigate Potential Threats to the Semiconductor Industry
As mentioned above, companies in the semiconductor industry chain are hyperconnected, and supply chain security is already a problem that the semiconductor industry must fully understand and response. The National Institute of Standards and Technology (NIST) released a new version of the document SP 800-161r1[8] on cybersecurity supply chain risk management in May 2022 to help all circles understand supply chain risks and guide enterprises to effectively manage risks. The document pointed out that supply chain security risks may come from: 1. Theft of confidential information by system integrators insiders, 2. Agents working for the specific country put malware into products provided by suppliers, and 3. Reuse of vulnerable code, and went on to propose 18 domains for effective management of supply chain cybersecurity risks.
In order to improve the security of the semiconductor industry supply chain, in January of 2022, SEMI took the next step and launched their new SEMI E187 specifications for the cybersecurity of fab equipment standards. These standards were designed to neutralize supply chain attacks, insider threat, and other potential flash points in a cyber-attack. Through SEMI E187, it is possible to provide global semiconductor equipment manufacturers with a guideline for security by design at early stages. Secondly, enterprises can also clarify cybersecurity requirements when purchasing equipment to avoid the new asset becoming a security risk. Dr.Terence Liu, CEO of TXOne Networks and a member of the SEMI Taiwan Semiconductor Cybersecurity Committee, has said, “The establishment of this standard is like building a trust mechanism. Semiconductor manufacturers can trust that the equipment handed over by suppliers is safe.”
TXOne’s specialists have collaborated with industry leaders to create a new approach to management based on applying OT zero trust to the asset life cycle. By zeroing out trust and implementing a policy of verification at every phase that could present a potential point of entry to a threat, cybersecurity specialists can streamline compliance with SEMI E187, address OT cybersecurity challenges, and secure fab equipment against cyber threats.
1) Zero trust for inbound devices:
This cybersecurity policy takes effect from the moment a device comes onto your premises. Newly-arrived assets being prepared for onboarding should also be pre-scanned (Trend Micro Portable Security 3 Pro™) to mitigate the risk of supply chain attack – in the past, cyber attackers have triggered cyber incidents by compromising devices prior to shipment.
2) Zero trust for appliances:
Traditional antivirus software can bog down assets, leading to crashes or delays. Operations-friendly, “OT-native” lockdown software (StellarEnforce™) secures legacy endpoints with a trust list that only allows applications critical to operations. For modernized endpoints that carry out more varied or complex tasks, a library of trusted ICS applications and licenses informs next-generation antivirus software (StellarProtect™) as to which files and applications it can skip and give priority to, preserving resources for operations.
3) Zero trust for networks:
Attackers find your OT network much more challenging to attack when unnecessary “doors” in the network are sealed with specific rules for traffic put in place by firewall or IPS appliances (EdgeIPS™ & EdgeFire™). With these special rules for traffic, which are based strictly on which assets need to communicate to do their work, the network is separated into segments that are easier to monitor and secure. For legacy and otherwise unpatchable assets, virtual patching shields vulnerabilities so that they cannot be exploited by attackers. Network appliances and policy are easily observed and maintained through a single, centralized console (OT Defense Console™).
References:
[1] PRESIDENTIAL ACTIONS, “Executive Order on America’s Supply Chains”, THE WHITE HOUSE, Feb 24 2021, Accessed May 30 2022
[2] Mark Lapedus.”200mm Shortages May Persist For Years”, Semiconductor Engineering, Jan 20, 2022, Accessed May 30 2022
[3] Lars Mönch, Reha Uzsoy, John W. Fowler, “A survey of semiconductor supply chain modelspart I: semiconductor supply chains, strategic network design, and supply chain simulation
part I: semiconductor supply chains, strategic network design, and supply chain simulation”, International Journal of Production Research, Oct 20 2017, Accessed May 30 2022
[4] Cadence Security Advisory, “Log4j Vulnerability Security Advisory”, Cadence, Accessed May 30 2022
[5] ASML PRESS RELEASE, “ASML recently discovered IT systems security incident”, ASML, May 1 2015, Accessed May 30 2022
[6] Toby Sterling, Anthony Deutsch, “ASML says it suffered intellectual property theft, rejects ‘Chinese’ label”, Reuters, Apr 11 2019, Accessed May 30 2022
[7] TXOne Networks White Papers, “Supply Chain Security: Are SBOMs Ready?”, TXOne Networks, May 26, 2022, Accessed May 30 2022
[8] Jon Boyens (NIST), Angela Smith (NIST), Nadya Bartol (Boston Consulting Group), Kris Winkler (Boston Consulting Group), Alex Holbrook (Boston Consulting Group), Matthew Fallon (Boston Consulting Group), “Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations”, NIST, May 5 2022, Accessed May 30 2022
[9] SEMI, “SEMI E187 – Specification for Cybersecurity of Fab Equipment”, Dec 28 2021, Accessed May 30 2022