Background
Cyber attacks on critical infrastructure have always been a severe threat. Among the critical infrastructures, one obvious concern is the health industry – cyber attacks will undoubtedly affect people’s medical care and life safety. Especially during the COVID-19 pandemic, the global demand for medical care is strained, and even a short interruption of services or equipment operation can have irreversible consequences for patient populations.
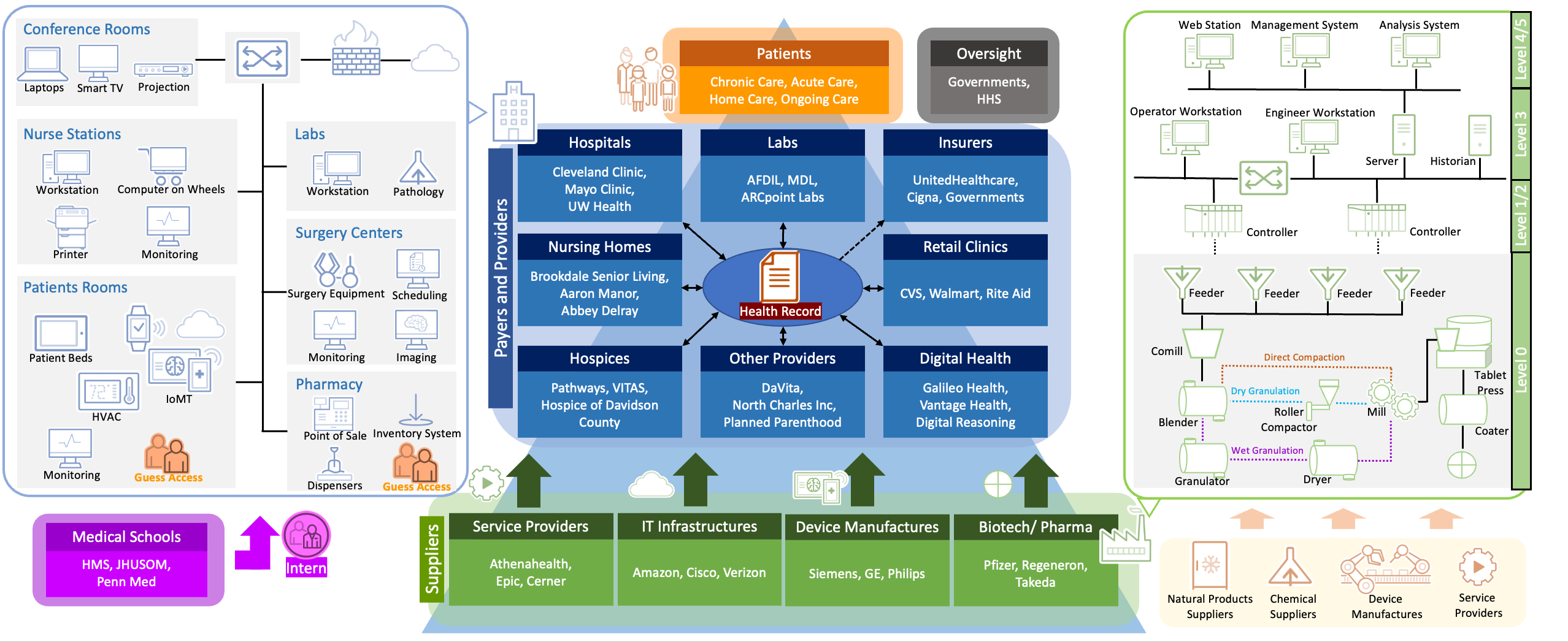
Healthcare industry services are diverse and large-scale, covering public and private sectors. The overall ecosystem structure (as shown in the figure below) is based on providing patients services to meet their specialized needs (such as chronic care, acute care, home care, ongoing care, etc.). The industry’s midstream (the blue area in the figure) is Healthcare Payers and Providers, which consist of hospitals or nursing centers that directly provide medical-related services to patients, etc., and include insurance companies that manage the payment of medical services. Companies in this region often come into contact with health records that should be specially protected due to their handling of patient care, eligibility, or claims. These data are not only actively provided by patients, as there is also a need to share patients’ prescription drug records between hospitals and nursing centers or to send patients’ pathology to laboratories for analysis. Providers will also transmit or access health records to each other.
To ensure the regular operation of healthcare services, there will also be various suppliers (as shown in the green area in the figure) that meet different needs, including manufacturers of drugs for hospitals, nursing centers, and retailers, manufacturers of medical equipment such as surgery, monitoring and recording, and providers of information software and cloud services. Since the healthcare industry is directly related to the health and safety of citizens, each country will have specific government departments to supervise to ensure that citizens can obtain stable medical quality and avoid the arbitrary abuse of protected data. In this complex ecosystem, it is easier for hacker groups or state-sponsored hackers based on personal interests to attack specific targets in the industrial ecosystem.
As mentioned above, the healthcare industry does not allow service interruption, like all critical infrastructures, and it also involves protected health records in the storage and exchange of data between healthcare payers and providers. In addition to exposing the public to the risk of extortion, misuse of this information may even pose a national security threat if used by terrorists or malicious individuals. For this reason, the United States has promulgated the Health Insurance Portability and Accountability Act (HIPPA) Act [1], which stipulates in detail that the healthcare industry, whether suppliers or insurers, there must meet strict cybersecurity requirements for the transmission, access, or storage of protected data. Thus, any healthcare company should manage its own cybersecurity to avoid exposing the company and the public to threats.
Threats Facing the Healthcare Industry
Due to the huge scale of the ecosystem involved in the healthcare industry, from medical centers (high-scale medical institutions) that directly provide medical services to private clinics or biotechnology companies funded by the state to small start-ups, they all have health information or drug research and development achievements related to people’s and national safety. Any cyber threat may lead to the death of patients or the failure of drug R&D/manufacturing. Looking at the medical institutions and pharmaceutical manufacturers that may directly cause the above impact, the left half of the picture is the typical network architecture of medical institutions.
We can find that the network architecture of medical institutions is flat, but it contains many departments, including Conference Rooms for non-core business to Surgery Centers and Patient Rooms of the medical core. Any network interference between them will cause varying degrees of impact, and some departments can be opened to guest access, which makes it more difficult for medical institutions to close the network inside. The right half of the picture is a typical network architecture for pharmaceutical manufacturers. Its composition is similar to a standard industrial control environment, including workstations, controllers, historians, field devices, management systems, and other servers. It is also not allowed to interrupt the demand, which makes the device itself unable to be in a safe state due to less maintenance or patches. Therefore, TXOne Networks analyzes the current situation of drug R&D manufacturers, medical institutions, and their related supply chains and finds the following potential threats:
1. Healthcare industry lacks vulnerability monitoring mechanisms, making it difficult to control vulnerabilities of diverse products and services effectively
The high development cost, long R&D cycle, high failure risk, and high technical threshold required for pharmaceutical manufacturers to develop drugs make intellectual property (IP) with high commercial value one of the targets of hacker organizations. In response to various countries’ tariff and protection policies, early pharmaceutical manufacturers set up factories in multiple countries. However, the influence of globalization drives tariffs to decrease dramatically, such that global factories have turned to the level of product lines before engaging in global sales [2].
In a highly globalized pharmaceutical company, the information software used by each unit is heterogeneous due to the different times of informatization of each branch. Commonly information systems used in the pharmaceutical industry include Sage X3, SAP, BPCS, TETRA or SEAMS, and other companies’ management systems. However, one of the systems, called Sage X3’s Enterprise Resource Planning (ERP), has been found by researchers to have a vulnerability that can be executed by attackers to achieve Remote Command Execution (RCE) [3]. If the vulnerability is exploited, it will directly affect the pharmaceutical formula management, tracking, control, and review processes (Level 4 and Level 5 in figure 1) and then affect the production of drugs.
In addition to information software, in pharmaceutical manufacturing, as in most industrial control environments, many old or non-renewable assets are used (the Level 0 position in the right half of the picture), which makes traditional system vulnerabilities continue to exist. In 2017, the NotPetya ransomware caused $870 million worth of losses to the Merck pharmaceutical company by penetrating Microsoft systems without security patches, and the ransomware also affected production facilities, resulting in the production of the HPV vaccine Gardasil 9 being unable to meet yearly demand that year [4][5].
Similar to pharmaceutical manufacturers, larger medical institutions will also introduce much different information software or medical equipment according to the needs of different departments, such as Surgery Equipment, Monitor Devices, Scheduling Devices, and Imaging Devices in the left half of the picture, especially in The introduction of technologies such as the Internet of Things, artificial intelligence and cloud computing, more various wearable devices or cloud services make the situation more chaotic. The U.S. Department of Health and Human Services (HHS) also explained security risks for wearable devices in the HHS Cybersecurity Program, which contains many disclosed cybersecurity vulnerabilities [6]. In 2021, Kaseya IT service provider also became the victim of the extortion software attack by the REvil group due to software vulnerabilities and impacted medical institutions [7].
The above scenario description shows that there are many software, manufacturing equipment, and medical equipment in the healthcare industry, and most of them do not allow service interruption. To better manage the vulnerabilities in the operational environment, enterprises should adopt a software bill of materials (SBOM) [8], technologies such as virtual patching (through network-level vulnerability protection), not only allow asset owners to respond quickly to newly discovered vulnerabilities but also allow devices to continue to operate in the face of vulnerabilities.
2. Due to the extensive use of endpoints by the healthcare industry, a visual and central management mechanism is required to manage security information
Generally, pharmaceutical manufacturers’ cyber-physical system (CPS) is a highly complex network. A production area will use multiple industrial control systems, each with its network structure. Taking a production line as an example, it has nearly 100 workstations or servers. Besides, large health facilities will also need to manage thousands of endpoint devices depending on the medical resources and the number of patients they can accommodate. In particular, the patients’ rooms and pharmacy of the health facility are open to visitors to directly contact the equipment, which makes the cybersecurity team unable to trust the requests from any equipment. In the environment of pharmaceutical manufacturers and health facilities with many devices, visualized and central management is required to manage information such as network logs, security events, and device information. Meanwhile, machine learning methods should be used to avoid untrusted requests from devices that hackers have compromised.
3. Different systems in the healthcare industry require network segmentation and management to minimize the impact of risks
In recent years, mergers and acquisitions have been one of the business trends of pharmaceutical manufacturers [9]. Under the M&A process, the new network is connected to other research sites or factories, which makes the network structure more complex. If the network cannot be effectively divided and managed according to actual needs at this time, it is easy to cause continued cybersecurity risks. Similar to the NotPetya ransomware attack on Merck, the ransomware spread to R&D, manufacturing, and sales departments through the internal network, causing 30,000 devices to lockdown.
Medical care institutions mainly focus on core business, and most non-core businesses such as cleaning, physical security, or waste disposal will adopt an outsourcing strategy. In 2011, a hospital in Texas had a security guard downloading malware on devices with health information [10] (refer to Nurse Stations of figure 1). If the malware continues to spread to the medical centers and patients’ departments, it will cause incalculable consequences. However, it is worth noting that some medical care institutions in rural and suburban areas may also outsource core medical businesses, such as diagnosis and treatment, due to talent recruitment difficulties. It will make it more difficult for departments to control cybersecurity. Thus, in a medical care institution with a relatively flat network structure, it is necessary to carry out effective network segmentation and management for each department or service so that the impact caused by cyber attacks remains limited to small areas except spreading to the entire medical service.
4. The Healthcare industry does not have security controls on devices entering the network environment, resulting in continued exposure of the internal network to high-risk threats
The internal staff of medical care institutions is quite diverse. In addition to doctors and nurses, it also includes much administrative staff, medical assistants, and interns (such as students in the college of medicine). However, most healthcare organizations do not restrict personnel from bringing their own devices into the internal network, causing healthcare facilities to be exposed to high-risk threats. This is especially the case when such PCs are used not only to connect to the academic network but also to download third-party software or use a USB that contacts with other insecure devices for research needs.
Researchers download third-party software or make contact with insecure environments, which gives attackers more opportunities to implant malware in medical care institutions. According to Trend Micro’s 2021 Annual Cybersecurity Report, Healthcare is one of the top three industries most frequently attacked by ransomware [11].
Even though LockBit, a known recently active ICS ransomware group, claimed they would not attack healthcare, educational, or charity institutions, attacks on healthcare were recorded in 2021 that are suspected to be connected to this organization according to TXOne and TrendMicro research [12][13]. Medical care institutions, like most ICS environments, have many critical legacy assets that they are not allowed to patch, such as diagnostic equipment in operating rooms or monitoring equipment in emergency rooms, which any interruption will directly affect life safety. To prevent malicious devices from entering the internal network, pre-scanning for malware and up-to-date security configurations and policy for when devices enter the medical institution are necessary.
5. It is difficult to effectively protect health records within the healthcare industry, leaving many people at risk of extortion or life-threatening situations
The average cost of a data breach in the healthcare industry in 2021 is $9.6 million [14], which is obviously one of the biggest challenges facing the healthcare industry. In addition to external attacks, cybersecurity incidents are more likely to result from insider threats in medical institutions. The reason is that most doctors authorized by the state do not have time to deal with registration or paperwork, so they provide personal credentials to multiple nurses or medical assistants, which in turn causes an unmanageable risk of data abuse.
Sometimes nurses or medical assistants may misuse health data simply out of curiosity or to provide further services to patients, but there is no guarantee that the data will be leaked in large quantities for economic benefits or other reasons. As a result, in addition to strictly abiding by relevant regulations and conducting cybersecurity training, medical institutions should also harden the endpoint cybersecurity of devices that process health data so that the devices can only execute permitted applications or services. They should furthermore improve restrictions on access to data to mitigate the impact of the data breach.
6. The workforce shortage in medical institutions has caused violations of cybersecurity policies and increased the risk of external attacks
Throughout the pandemic, the medical workforce has been spread thin and heavily burdened with work, leading some healthcare specialists to violate medical institutions’ policies or set up remote services within the hospital by themselves. Doctors can still access sensitive data through remote connections to the hospital at home or when supporting other institutions through this service. In this case, remote access makes the protected data no longer locked in the internal network so that external attackers could carry out cyber attacks on medical institutions. To avoid such risks, medical institutions should not only make a trust list of connected devices but also identify relevant network protocols and the content of communications to avoid violations of medical institutions’ cybersecurity policies.
With the application of technologies such as the Internet of Things, artificial intelligence, and cloud computing to the healthcare industry, medical institutions, government, and people will no longer only provide health records to testing laboratories but also provide data to diverse third-party organizations in response to the needs of data analysis, personal health management, virtual nursing, or telemedicine. Especially during the pandemic, digital health [15] has become an important emerging industry for healthcare. Under such a large amount of data sharing, assuming third-party organizations become victims of cyber attacks, these shared data are likely to be exposed. For example, many information security vulnerabilities in wearable devices and applications often used in personal health management and health care have been successfully exploited by malicious actors [3]. In 2018, there was even a MyFitnessPal application data leakage incident, in which TXOne Networks Researchers reported that more than 150 million valid items of user data were leaked including account numbers, emails, and password hashes [16]. For health records that are difficult to manage centrally, each enterprise needs to rely on each to manage its information security. When Healthcare Providers or government units choose a third-party organization for data analysis or other medical needs, they should also do their due diligence on cybersecurity for correct evaluation [17].
How to Mitigate Potential Threats to the Healthcare Industry
As mentioned above, the healthcare industry is related to the health records of people and national leaders, which is closely related to national security. Simultaneously most medical services do not allow service interruption, so companies in the healthcare industry should establish a secure cyber-physical system environment.
Apart from compliance with the local medical regulations and Health Insurance Portability and Accountability Act (HIPAA) standards, the National Institute of Standards and Technology (NIST) also developed a framework for improving critical infrastructure cybersecurity, which heeded the appeal from the American Hospital Association and other medical-related organizations to provides enterprise network a risk management [18][19].
Besides, HHS also released Health Industry Cybersecurity Practices (HICP) [20] for the healthcare industry based on the NIST Cybersecurity Framework (NIST CSF), which describes the cybersecurity threats and mitigation practices faced by the healthcare industry.
TXOne’s specialists provide recommended technical solutions based on HICP best practices. Admittedly, the technical solutions are not intended to be comprehensive but are rather meant to be considered as part of an organization’s overall cybersecurity program. Further, the technical solutions introduced in this paper strengthen cybersecurity capabilities in healthcare industries by:
1) Endpoint Protection Systems:
The traditional endpoint security protection is not developed for the medical operation system, which may occupy not only the huge hardware resources of the system but also lack sufficient visibility. However, OT-native endpoint protection systems can secure modernized and legacy endpoints side-by-side. For a modern healthcare operation system, StellarProtect is Industrial-grade next-generation endpoint security for ICS. Purpose-built all-terrain ICS protection and combined machine learning technology defend against known and unknown malware attacks, including zero-day vulnerabilities. For a legacy healthcare operation system, StellarEnforce adapts an application trust listing technology for the legacy asset, and it is also equipped with unique locking technology to ensure operational security, including operation lock, USB device lock, data lock, configuration settings lock, which can completely protect complex and numerous endpoints in healthcare operation.
2) Asset Management:
The traditional asset management solution needs to install the agent on the client, which is unsuitable for air-gapped environments. The OT environment of some medical industries is similar to that of a factory – for example, the pharmaceutical factory’s production line or the hospital’s detection system, including ultrasonic instruments, nuclear magnetic resonance, computed tomography (CT) instruments, and so on, are all critical OT systems. Not only is the replacement cycle quite long, but it is also challenging to detect weaknesses and viruses. Trend Micro Portable Security 3 Pro (TMPS3) is an installation-free inspection scanning and clean-up solution for air-gapped systems and standalone computers. Implement TMPS3 in the cyber security plan to achieve the objective of mitigating the risk of malicious code being introduced. It generates an inventory for all scanned assets, including OT-connected assets such as laptops, desktops, and diagnostic test equipment that may interface with or run applications that support CPS systems and is capable of transmitting executable code to connected assets.
Meanwhile, TMPS3 generates detailed information about all scanned assets while scanning. This asset information includes comprehensive details of each asset, including IP address, MAC address, hostname, OS version, patch list, installed application list, and so on.
In terms of procurement, technicians use TMPS3 devices to verify suppliers’ OT assets and service vendors’ laptops for regulatory compliance. Inspect incoming or outgoing devices, conduct pre-shipment inspections, and conduct regular internal inspections for supply chain assessment. As TMPS3 conducts these scans, it collects asset information to enhance OT visibility insight, while the ‘Pro’ edition of TMPS3 comes additionally equipped 64GB of AES-256 encrypted storage for secure file transfer.
3) Network Management:
With IT and OT converging, threats can potentially be delivered or a convenient back door can be introduced that allows hackers into customers’ operational environments. Many network defense solutions are on the market but are not specific to OT environments. TXOne’s Edge series is designed for use in levels 1-3, both in front of mission-critical assets and at the network edge. In addition, the TXOne Edge series provides micro-segmentation to divide the network of high-risk OT systems into smaller network units and control communication between specific servers and application services. It can help the security team limit the impact of a cybersecurity incident and reduce the lateral movement of hackers across the internal network. Especially, it can sense customers’ network traffic and production assets, and every appliance in TXOne’s Edge series fits right into the customer’s network without disrupting operations.
Every OT network needs an Intrusion Prevention System (IPS). If set in “monitor” mode, IPSes will monitor network traffic using signature-based tracking and rules set by the administrator. For example, the Edge series’ core technology for One-pass Deep Packet Inspection for Industrial (TXODPI) allows the customer to create and edit trust lists, allowing for interoperability between key nodes and deep analysis of L2-L7 network traffic. It enables customers to control the connections and content transmissions between various network equipment assets to ensure that unauthorized devices cannot establish connections or transmit content.
4) Vulnerability Management:
Due to the availability and long replacement cycle of healthcare equipment, it is often difficult to repair even if vulnerabilities are found. Consequently, the OT environment has become an entry point for attackers to penetrate the hospital and pharmaceutical industry. TXOne’s Edge series can shield them from attack with no changes to the asset. Virtual patching shelters endpoint and network vulnerabilities, while signature-based antivirus provides an extra layer of protection under EdgeIPS Pro.
5) Incident Response:
The success of incident response depends on tracking, compiling, and documenting system security incidents, including maintaining records about each incident, including audit monitoring, network monitoring, physical access monitoring, user and administrator reporting, and reported supply chain incidents:
StellarOne allows management from a single pane of glass with support for Syslog forwarding, indicators of compromise (IoC) integration, and centralized monitoring.
The OT Defense Console (ODC) platform gives comprehensive visibility of the connected, air-gapped, and standalone OT environment using Edge series products. ODC is a centralized management platform for multiple sites for each deployed Edge series product.
The TMPS3 collected asset information can be to the CSV format through the centralized management program as an asset inventory or sent to a SIEM or Rsyslog server for further asset management such as maintaining OT asset inventory or identifying impact levels, known vulnerabilities, and cyber risks.
6) Medical Device Security:
Internet of Medical Things (IoMT) technology has become popular in the medical industry, and these connected medical devices will remote patient data collection. These devices rarely come equipped with endpoint protection or vulnerability management. StellarEnforce prevents malicious software from running on purpose-built systems, strictly adhering to pre-approved software by using application trust listing. It solves the problem that traditional antivirus software cannot be installed on medical devices. Besides, with the installation-free TMPS3, healthcare companies can easily plug the scanning tool into a medical device to achieve the objective of mitigating the introduction of malicious code.
References:
[1] ASPE, “Health Insurance Portability and Accountability Act of 1996”, U.S. Department of Health and Human Services, Aug 20 1996, Accessed Jun 14 2022
[2] Pasteur Lin, “Supply Chain Management of Global Pharmaceutical Companies: A Case Study Approach“, National Chiao Tung University, Jun 2004, Accessed Jun 14 2022[3] Tara Seals, “Critical Sage X3 RCE Bug Allows Full System Takeovers”, Threatpost, July 7 2021, Accessed Jun 21 2022
[4] Eric Palmer, “Merck has hardened its defenses against cyberattacks like the one last year that cost it nearly $1B”, Fierce Pharma, Jun 28 2018, Accessed Jun 21 2022
[5] David Voreacos, Katherine Chiglinsky, Riley Griffin, “Merck Cyberattack’s $1.3 Billion Question: Was It an Act of War?”, Bloomberg Markets, Dec 3 2019, Accessed Jun 21 2022
[6] HHS CYBERSECURITY PROGRAM, “HC3 Intelligence Briefing Wearable Device Security”, U.S. Department of Health and Human Services, Mar 5 2020, Accessed Jun 14 2022
[7] Charlie Osborne, “Updated Kaseya ransomware attack FAQ: What we know now”, ZDNet, July 23 2021, Accessed Jun 21 2022
[8] TXOne Networks White Papers, “Supply Chain Security: Are SBOMs Ready?”, TXOne Networks, May 26 2022, Accessed May 30 2022
[9] Vikrant Doshi, Rushabh K Shah, “Current Pharma M&A Trends”, Deloitte, Mar 2022, Accessed Jun 21 2022
[10] Vikrant Doshi, Rushabh K Shah, “Insider Threats: In the Healthcare Sector”, Center for Internet Security, Oct 10 2016, Accessed Jun 21 2022
[11] Trend Micro Research, “Navigating New Frontiers: Trend Micro 2021 Annual Cybersecurity Report”, Trend Micro, Mar 17 2022, Accessed Jun 14 2022
[12] Hank Chen, Mars Cheng, “Safeguarding OT environments against the LockBit 2.0 ransomware”, TXOne Networks, May 25 2022, Accessed Jun 28 2022
[13] Trend Micro Research, “Ransomware Spotlight: LockBit”, Trend Micro, Feb 8 2022, Accessed Jun 14 2022
[14] Joseph Johnson, “Average total cost per data breach worldwide 2021, by industry”, Statista, Nov 11 2021, Accessed Jun 14 2022
[15] Health topics, “Digital health”, World Health Organization, May 26 2022, Accessed Jun 14 2022
[16] Mars Cheng, YenTing Lee, Max Farrell, “ICS Giants of the Fortune 500: The Frequency and Risk of Data Exposure”, TXOne Networks, Dec 02 2021, Accessed Jun 14 2022
[17] HealthITSecurity, “The Importance of Third-Party Risk Assessments in Healthcare”, HealthITSecurity, Nov 01 2021, Accessed Jun 14 2022
[18] National Institute of Standards and Technology, “Framework for Improving Critical Infrastructure Cybersecurity”, National Institute of Standards and Technology, Apr 16 2018, Accessed Jun 17 2022
[19] Susan D. Hall, “NIST cybersecurity framework: How it will impact healthcare“, Fierce Healthcare, Feb 14 2014, Accessed Jun 14 2022[20] HHS 405(d) Program, “Health Industry Cybersecurity Practices”, U.S. Department of Health and Human Services, Accessed Jun 14 2022